When you sign up on most websites, your data will be stored in a database table. This table will typically include your username, email, password and any other details the website has on you.
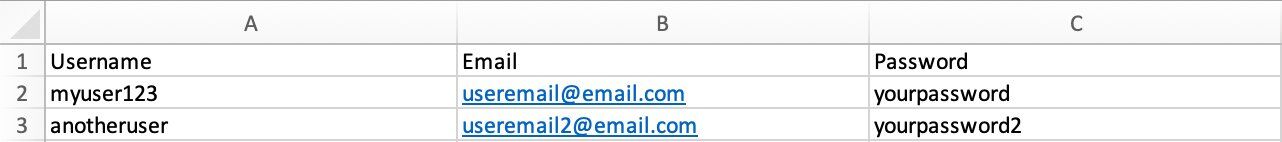
Each time you return to the website and try to log in, the user table will be cross-checked against what you have inputted to find a match. Thousands of users can be stored in a single table so they are a key target for hackers looking to exploit the data and sell on via a black-market.
Passwords
The safest presumption we can make is that your password will be passed to a hacker at some point or someone with malicious intent. Commonly, a third-party website you use will be exploited and reveal your email and password in a leak. Many high-profile cases of data leaks have been highlighted over the years in the media.
You can check if your email has previously been included in a data breach via the website found here.
Best practices for passwords:
- Change your password frequently. This will invalidate older passwords that might fall into the wrong hands and render the old data useless.
- Make them unique to each site. If your username and password details are leaked, someone with malicious intent will likely attempt to use them on other popular websites. If the password is unique, in every case, you will minimise exposure.
A reasonable format for a password might be: MYPASSWORD_WEBSITENAME
Two-tier Login
Most users will be familiar with 'Two-Tier Login' through their bank. In the payment processing industry, this has been a key access requirement for a number of years and ensures a password leak alone cannot enable a third party to access an online account. A password is used in combination with a fob, key-card or text message to gain access. Phone applications are becoming increasingly popular for this purpose. Google Authenticator is one such application that most sites now readily support.
SSL Certificate
When you input data into a website, you will enter the data as it is. This type of data is unencrypted and 'plaintext'.
e.g
'mypassword'
An SSL certificate is commonly installed on a website to encrypt the data that is inputted until the point of intended decryption. This is done to ensure data (plaintext) cannot be easily deciphered as it is transmitted. When you enter credit card details or password, you should always ensure the web page indicated the sensitive data will be encrypted. SSL encryption is commonly indicated by the padlock icon in the URL bar like this:
SSL certificates are installed on a server for this type of encryption and they are commonly renewed annually. Most server software now allows for a free SSL service. There are however other premium options available.
Security Basics for the Web Designer
Here are some additional basic security steps for the web designer.
Scope
There are potentially many routes where a hacker might try to find an exploit. Typical sites include:
- Server Ports (FTP, SSH)
- Application Admin Panel (/admin or /wp-admin)
- Application Front-end (search bars or forms)
- Server Admin Panel (Plesk, CPanel)
It's difficult to oversee all these parts, all of the time. Therefore, the best way to mitigate risk is to minimise scope and block off access wherever possible.
Server Ports
Use a Firewall to block off access to all IPs with the exception of those that need it. Typical server admin programmes like Plesk and CPanel will allow you to do this easily. FTP and SSH are targeted regularly so blocking these will avoid a break-in and also improve your website speed.
Application Admin Panel
Again, as with port blocks, you could restrict these vulnerable parts with an IP block directive added to the htaccess file or server config file.
Application Front-end
Minimise plugins where possible and regularly update them. A quarterly upgrade plan is a good method to to follow if you can.
Server Administration Panel
Similar to the above, these panels can be limited by IP. If it's difficult for you to get a fixed IP (by way of a VPN), a two-tier add-on could suffice.
Other Security Techniques
Rate limiting
Most application firewalls will ensure a rate limiter to check traffic and throttle brute-force attacks in real-time. For example, if a password is incorrectly inputted more than x times, a block will occur on the IP to stop further guesses.